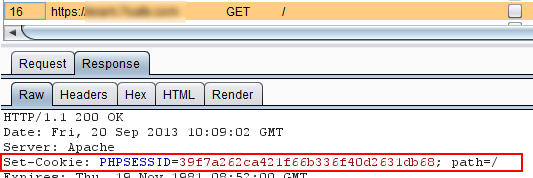
Often a combination of security flaws come together to produce a unique attack vector. Individually the flaws may not amount to much but together they make an interesting combo. This is invariably more interesting from a pentesting point of view because you know that a tool couldn’t positively find it. Session fixation is one such scenario because usually a few requirements must be met for the attack to work. I thought I’d write up a recent session fixation flaw because the act of forcing the cookie onto the victim involved a little twist on overwriting session cookies that made a reflective XSS attack last a lot longer while also laughing in the face of httponly. Continue reading
Session Fixation and XSS Working Hand-in-Hand
Leave a reply